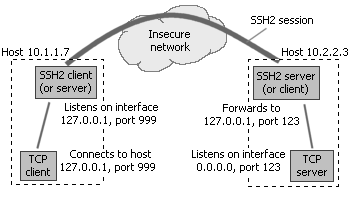
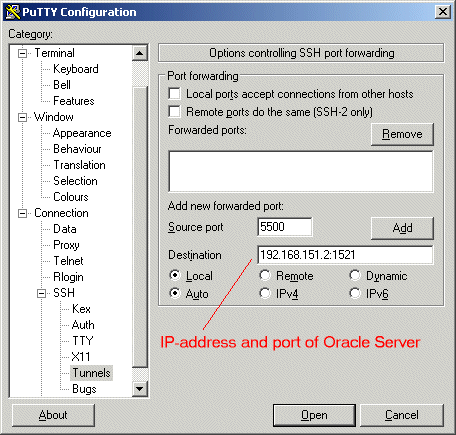
Welcome to the homepage of FileZilla®, the free FTP solution. The FileZilla Client not only supports FTP, but also FTP over TLS (FTPS) and SFTP. It is open source software distributed free of charge under the terms of the GNU General Public License. You configure the SSH client with the following client-to-server port forwarding rule: for each connection that comes on interface 127.0.0.1 and port 999, forward that connection to the SSH server, and request the SSH server to forward that connection to host 127.0.0.1 (relative to the server), port 123. Either edit /etc/ssh/sshdconfig & don't forget to restart SSH (service sshd restart) or leave it on 22, but forward port 26 on the router to port 22 on the second machine. Also, don't forget to change any firewall settings on the second machine to allow the connections through.
Bitvise SSH Client comes with several command line SSH clients that can be run unattended from other programs, or from the Windows Task Scheduler:
- Use sftpc for unattended file transfers.
- Use sexec for remote command execution.
- Use stnlc for unattended port forwarding/tunneling. See also our page about running stnlc as a service.
In addition, the following clients also offer a command line interface, but are usually used interactively:
- stermc provides a console-based terminal shell.
- spksc allows command-line management of client authentication keypairs configured for a user at an SSH server. (Requires an SSH server that supports the SSH Public Key Subsystem; e.g. Bitvise SSH Server.)
Each of the above clients supports a large variety of command line parameters. Limewire android. For help, run each of the clients as follows:
Eagan driving test course map. sftpc -?
Or like this:
sftpc -? | more
Bitvise SSH Client also includes utilities retry and log:
- Use the retry utility to repeat an SSH client session, another program, or a command script.
- Use the log utility to record the output of an SSH client session, another program, or a command script.
For help, run either of these commands without parameters. For example:

retry
The commands can be chained. For example:
log -tcxo C:DirLog retry -f=100,101 sftpc -profile=C:DirProfile.bscp cd /dir; put *.txt
This will retry an upload a default number of times, or until it succeeds; and record all output with timestamps, in log files of the form C:DirLog-(..).log.
The most common issue when using Bitvise SSH Client non-interactively occurs when the client is run under a different Windows account than was previously used interactively, and the client has no way to verify the server's host key.
Verification of the server's host key is essential to the security of the SSH session, so this step cannot be skipped. There are a number of ways in which the SSH Client can be told what host keys the server might use that the Client can accept:
- When you connect to the server interactively using the graphical SSH Client, and manually verify the server's host key, the SSH Client will store the host key in the Windows registry, but only for the currently logged on Windows user. All aspects of the SSH Client will then be able to connect to that server and trust that host key, as long as they are run in a Windows logon session belonging to the same Windows user.
- A host key can also be stored in a Bitvise SSH Client profile, and will then be trusted for the server connected to with that profile, regardless of the Windows logon session in which the connection occurs. If you have a host key that is trusted in the Windows registry, and you want to copy it to a profile:
- Open the profile using the graphical Bitvise SSH Client.
- Open the Host key manager interface from the Login tab of the SSH Client.
- Find the host key, right click it, and select Copy to profile.
- A host key or its fingerprint can be passed to any instance of the SSH Client - graphical or command line - using the following command line parameters:
- -hostKeyFile=..: Specifies a file in which one or more host keys are stored.
- -hostKeyFp=..: Specifies a SHA-256, Bubble-Babble, or MD5 fingerprint of a host key to trust.
If the server has multiple host keys, make sure that the unattended client has access to information about all of the host keys that the server might present. Otherwise, if the unattended client negotiates a different host key algorithm than the graphical client, host key verification may fail because the server will be presenting a different host key.
Like with host key verification, when the SSH Client is run unattended under a different Windows account than when the Client is used interactively, it cannot access authentication keypairs that are stored in a different Windows user's registry.
There are a number of ways an authentication keypair can be passed to the SSH Client when it's running under a different account:
In the graphical SSH Client that has access to the keypair, use the Client key manager to export the full keypair into a file. Then, log into the other Windows account, run the graphical SSH Client, and use the Client key manager to import the keypair. This will allow you to use the keypair under that account using the -pk=.. parameter.
Instead of importing the keypair using the other Windows account, you can also pass it directly to a command line SSH client using the -keypairFile=.. parameter. For example:
sftpc user@host:port -hostKeyFile=.. -keypairFile=.. cd /dir; put *.txt
A client authentication keypair can also be stored in a Bitvise SSH Client profile. To prepare a profile so that it will contain a keypair, open the graphical SSH Client that has access to the keypair. Configure host settings and use Save profile as to save the profile. Then, use the Client key manager, right click on the keypair, and select Copy to profile. If you do the same for the host key, using instructions in the previous section, you can then use the profile as follows:
sftpc -profile=C:PathProfile.bscp cd /dir; put *.txt
This assumes you configured Login > Authentication > Initial method to publickey, and the Client key setting to e.g. Profile 1 or Auto. As an alternative, you can use e.g. -pk=p1 on the command line to use the public key in location Profile 1.
OpenSSH is the open-source version of the Secure Shell (SSH) tools used by administrators of Linux and other non-Windows for cross-platform management of remote systems.OpenSSH has been added to Windows as of autumn 2018, and is included in Windows 10 and Windows Server 2019.
SSH is based on a client-server architecture where the system the user is working on is the client and the remote system being managed is the server.OpenSSH includes a range of components and tools designed to provide a secure and straightforward approach to remote system administration, including:
- sshd.exe, which is the SSH server component that must be running on the system being managed remotely
- ssh.exe, which is the SSH client component that runs on the user's local system
- ssh-keygen.exe generates, manages and converts authentication keys for SSH
- ssh-agent.exe stores private keys used for public key authentication
- ssh-add.exe adds private keys to the list allowed by the server
- ssh-keyscan.exe aids in collecting the public SSH host keys from a number of hosts
- sftp.exe is the service that provides the Secure File Transfer Protocol, and runs over SSH
- scp.exe is a file copy utility that runs on SSH
Documentation in this section focuses on how OpenSSH is used on Windows, including installation, and Windows-specific configuration and use cases. Here are the topics:
Additional detailed documentation for common OpenSSH features is available online at OpenSSH.com.
Putty
Ssh Connect To Different Port
The master OpenSSH open source project is managed by developers at the OpenBSD Project.The Microsoft fork of this project is in GitHub.Feedback on Windows OpenSSH is welcomed and can be provided by creating GitHub issues in our OpenSSH GitHub repo.
